
In today’s rapidly evolving cybersecurity landscape, no organization is entirely immune to cyberattacks. Despite the best preventive measures, some attacks may still break through and cause significant damage to an organization’s systems and data. When this happens, it’s critical to have a robust post-attack recovery plan in place. SentinelOne, a leading endpoint protection platform, plays a pivotal role in helping organizations recover from cyberattacks quickly and efficiently.
This article explores how SentinelOne’s advanced threat detection and response capabilities can aid organizations in recovering from cyberattacks, minimizing downtime, and preventing further damage to systems and data.
What is Post-Attack Recovery?
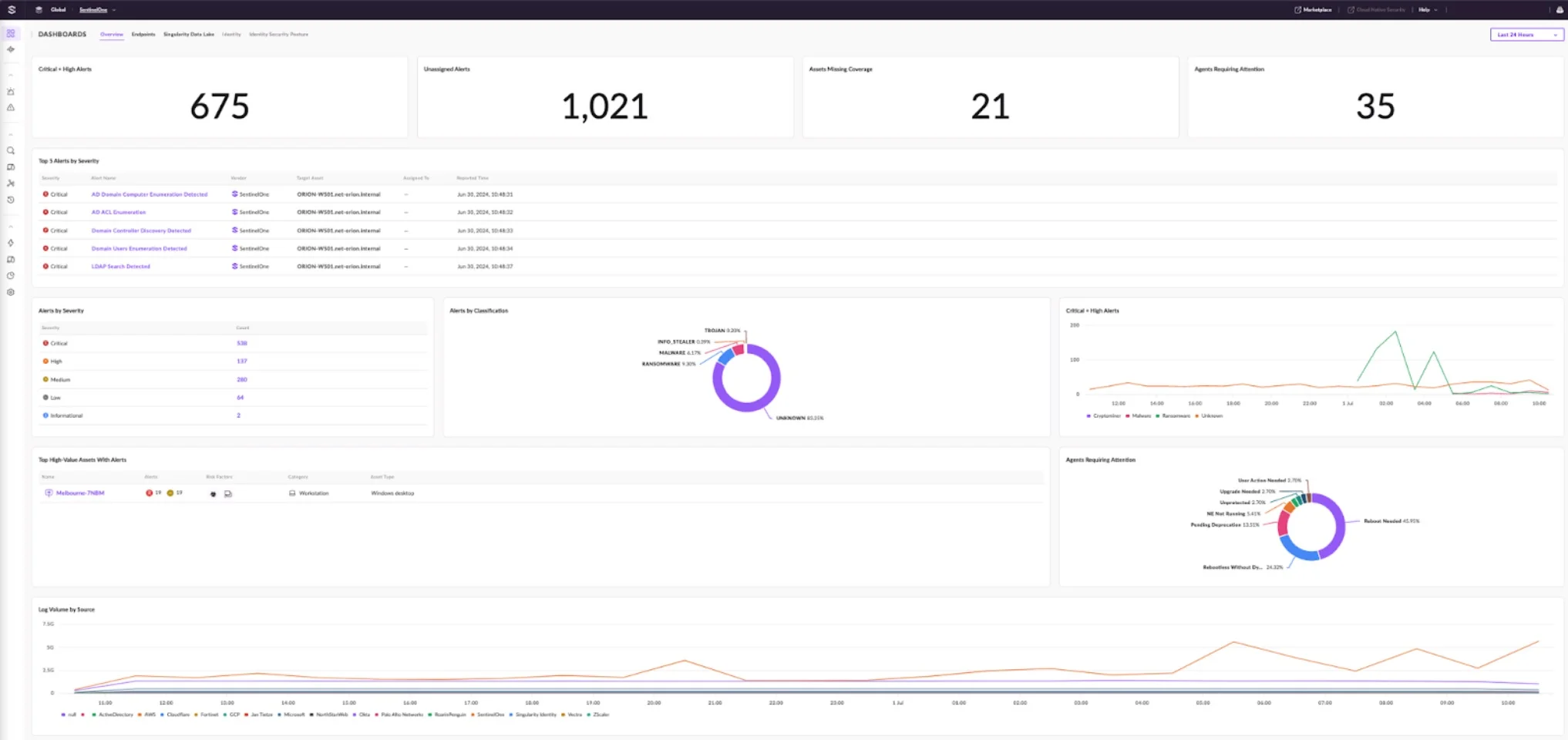
Post-attack recovery is refers to the series of actions taken after a cyberattack to restore normal operations, mitigate damage, and enhance security to prevent future attacks. A well-structured post-attack recovery plan typically includes:
- Identification and Containment: Detecting the attack early and containing its spread.
- Eradication: Removing the threat from all infected systems.
- Restoration: Recovering lost or compromised data and returning systems to normal functionality.
- Review and Strengthening: Analysing the attack’s cause and implementing additional measures to prevent recurrence.
During post-attack recovery, speed and efficiency are paramount. The longer it takes to identify, contain, and mitigate the attack, the more significant the damage can be, both financially and reputationally. SentinelOne’s capabilities can significantly improve the recovery process by providing advanced tools to detect, respond to, and recover from cybersecurity incidents.
SentinelOne: A Key Player in Post-Attack Recovery
SentinelOne provides autonomous endpoint protection, which is essential during both proactive threat prevention and post-attack recovery. With its real-time detection, AI-powered analysis, and automated response capabilities, SentinelOne can reduce recovery time and minimize the damage caused by an attack. Here are several ways SentinelOne aids in post-attack recovery:
1. Real-Time Detection of Threats
One of the critical components of a successful post-attack recovery process is the ability to detect an attack early. SentinelOne’s AI-driven platform continuously monitors endpoints for suspicious activity, including fileless malware, ransomware, and advanced persistent threats (APTs).
When a cyberattack occurs, SentinelOne’s real-time detection algorithms immediately identify malicious behaviour and notify security teams. The platform’s ability to detect both known and unknown threats in real-time helps organizations quickly pinpoint the source and scope of the attack, enabling faster containment and limiting the attack’s damage.
2. Autonomous Containment of Threats
Once a threat is detected, the next crucial step is containment. SentinelOne provides autonomous containment features that allow it to isolate compromised systems from the rest of the network automatically. By quarantining affected devices, SentinelOne ensures that the threat does not spread further, while also allowing security teams to focus on remediating the affected endpoints.
This automatic containment capability reduces the need for manual intervention, helping organizations mitigate risks quickly without disrupting ongoing business operations. SentinelOne’s isolated remediation process also enables rapid recovery, minimizing downtime and enhancing business continuity during the recovery phase.
3. Eradication and Remediation of the Threat
After containment, the next step in the recovery process is to eradicate the attack from the organization’s systems. SentinelOne’s platform goes beyond simply detecting and isolating threats—it is designed to completely remove malicious files, processes, and other indicators of compromise (IOCs) from infected systems.
SentinelOne leverages its behavioural AI to identify and eliminate any remnants of the attack, such as hidden malware, persistence mechanisms, or system modifications made by the attackers. By performing a deep scan and full remediation of infected endpoints, SentinelOne ensures that the threat is completely eradicated, reducing the risk of recurrence.
4. Restoration of Critical Systems and Data
Following the eradication of threats, organizations need to restore the functionality of their systems and recover any lost or compromised data. SentinelOne’s robust backup and recovery capabilities help restore systems to their pre-attack state. The platform allows organizations to roll back affected systems to a safe, known good state, based on previously stored snapshots or system backups.
This rollback feature is particularly valuable for recovering from ransomware attacks, where files or systems are encrypted or damaged. SentinelOne enables financial institutions, healthcare providers, and other industries reliant on sensitive data to quickly restore normal operations and avoid prolonged service interruptions.
5. Automated Post-Attack Forensics
Post-attack forensics is a vital part of recovery as it helps organizations understand the scope, impact, and cause of the attack. SentinelOne simplifies the forensic process by offering detailed logging and reporting features that provide security teams with insights into how the attack unfolded.
With SentinelOne, organizations can access a complete record of attack vectors, compromised systems, and executed malware. This forensic data is crucial for identifying the weaknesses that were exploited by attackers, helping organizations strengthen their security posture to prevent similar attacks in the future. Additionally, the information gathered can be used to comply with regulatory requirements or to assist in legal proceedings if needed.
6. Review and Strengthening Security Posture
The final phase of post-attack recovery is reviewing the incident and strengthening defences to prevent similar attacks in the future. SentinelOne helps organizations in this phase by providing continuous threat intelligence and offering recommendations to enhance overall security.
SentinelOne’s platform includes threat intelligence feeds that are updated regularly, helping organizations stay informed about emerging threats and attack techniques. The platform also supports proactive security measures, such as endpoint hardening and advanced threat hunting, which help prevent future attacks. By analysing the lessons learned from each incident, SentinelOne enables financial institutions, healthcare providers, and other organizations to implement more robust defences and adapt to evolving threats.
Benefits of Using SentinelOne for Post-Attack Recovery
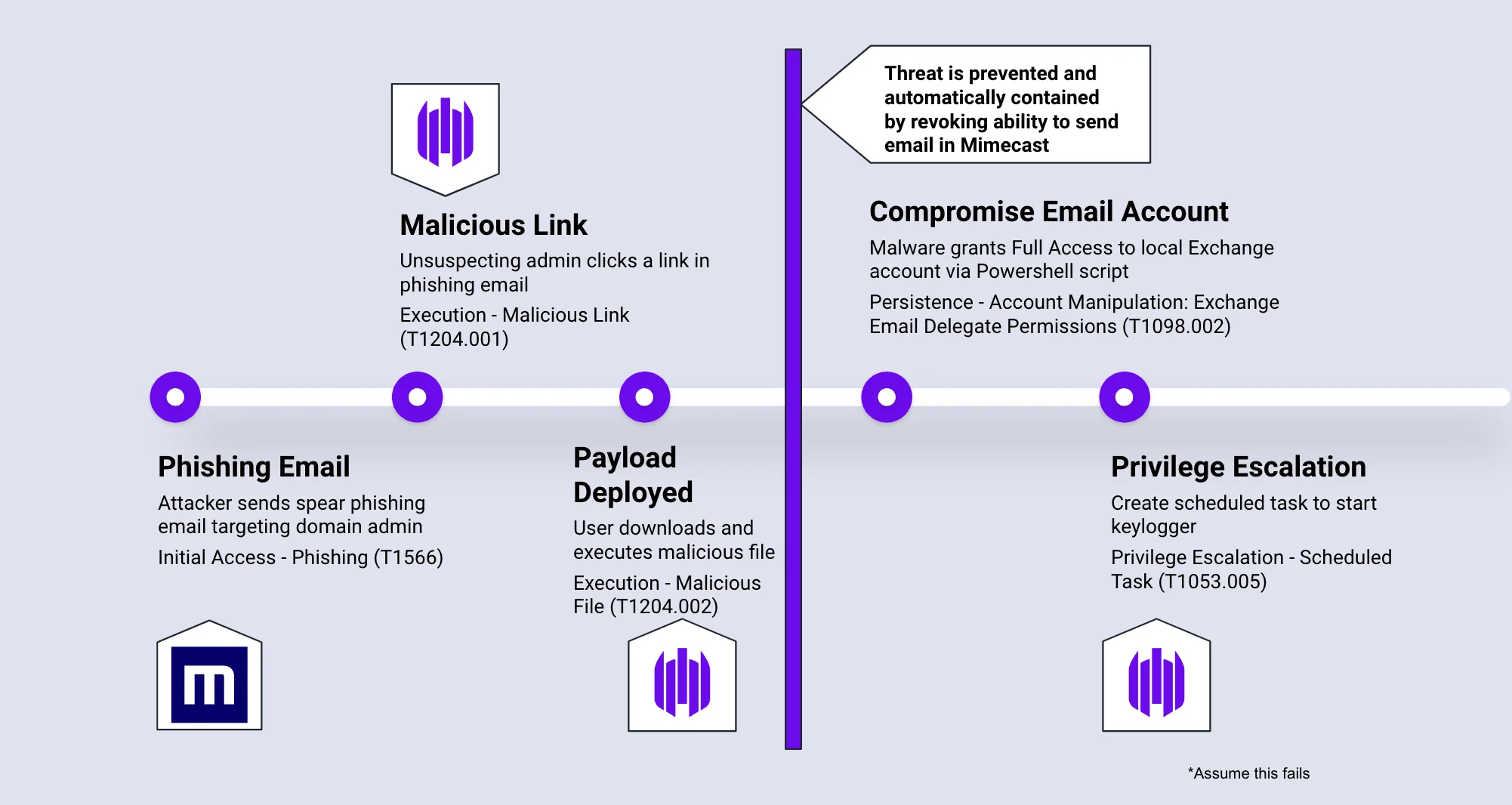
SentinelOne provides several advantages for organizations dealing with post-attack recovery:
- Speed and Efficiency: SentinelOne’s AI-driven automation significantly reduces the time needed to detect, contain, and remediate attacks, minimizing downtime and restoring systems quickly.
- Reduced Human Intervention: The platform’s autonomous response capabilities reduce the reliance on manual intervention, allowing security teams to focus on strategic tasks rather than dealing with every threat individually.
- Comprehensive Threat Remediation: SentinelOne’s ability to perform deep scans and remove all traces of an attack ensures that the organization is fully protected before systems are restored.
- Enhanced Forensics: SentinelOne’s detailed reporting and forensic capabilities provide organizations with critical insights into the attack, enabling them to learn from the incident and enhance their security posture.
- Improved Compliance: SentinelOne’s compliance features help organizations meet regulatory requirements, providing them with the evidence they need to demonstrate their security efforts during audits.
Conclusion
Post-attack recovery is a critical phase of cybersecurity that helps organizations minimize the impact of cyberattacks and restore normal operations. SentinelOne offers a powerful solution for post-attack recovery, providing organizations with real-time detection, autonomous containment, thorough eradication of threats, and seamless restoration of systems and data.
By leveraging SentinelOne’s AI-powered platform, organizations can ensure a faster, more efficient recovery process, minimize downtime and safeguard their reputation. With its comprehensive features for threat remediation and forensic analysis, SentinelOne empowers organizations to not only recover from attacks but also strengthen their defences against future threats. As cyber threats continue to evolve, having a reliable, AI-driven recovery solution like SentinelOne is crucial for any organization’s cybersecurity strategy.
If you need Post-Attack Recovery protection in your corporate and business, contact us here for more information.
