Check Point Advantages

Email Security Protection
Safeguards your organization’s email communication by blocking threats like phishing, malware, and spam.

Advanced Threat Intelligence
Check Point constantly updates its security systems using real-time data, ensuring protection against the most current threats.

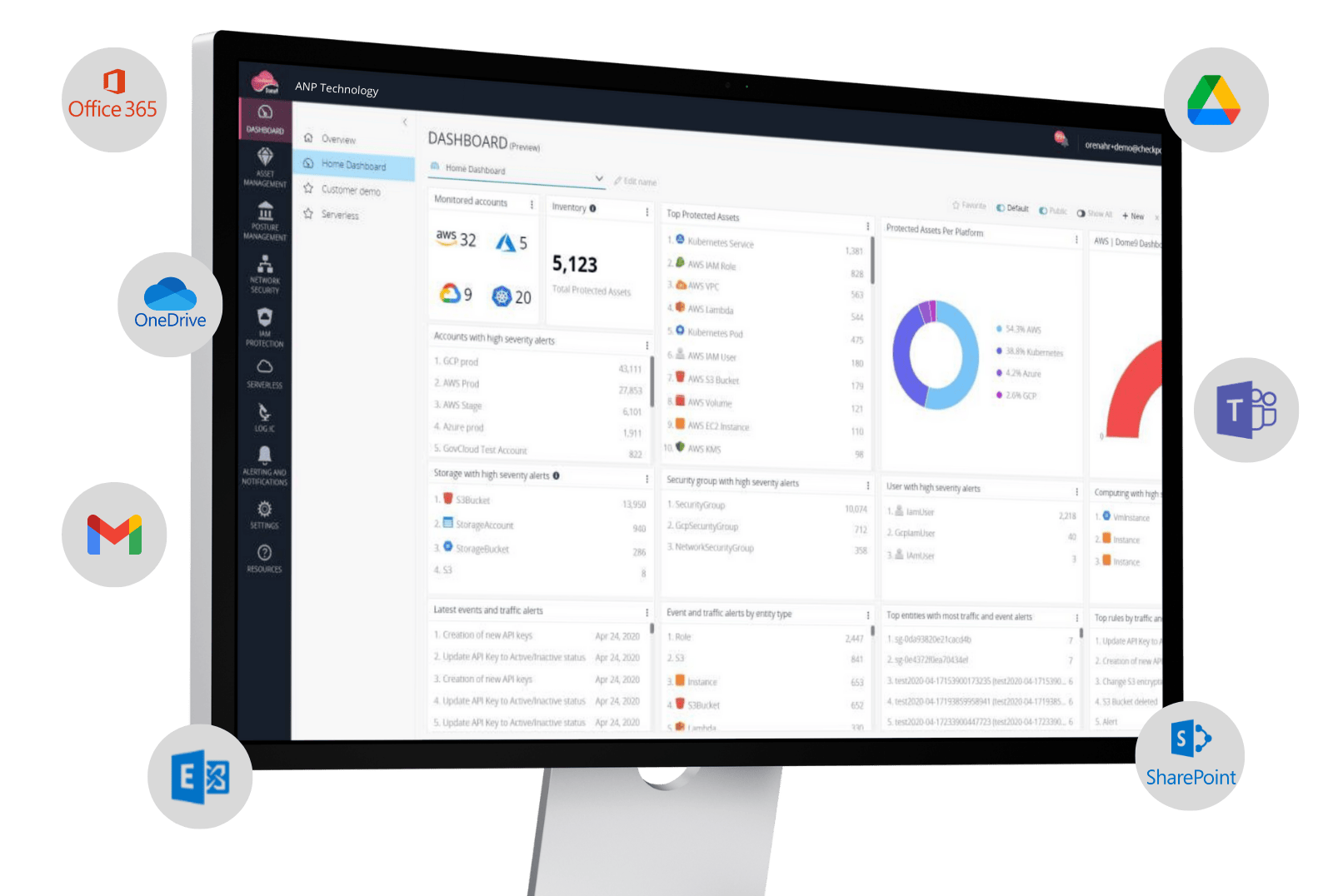
Protection to Collaboration Suites
Securing the tools and platforms used for team communication and collaboration, such as Microsoft 365 or Google Workspace.

Regulatory Compliance
Check Point’s products help businesses comply with various industry regulations, including GDPR, HIPAA, PCI DSS, and others.
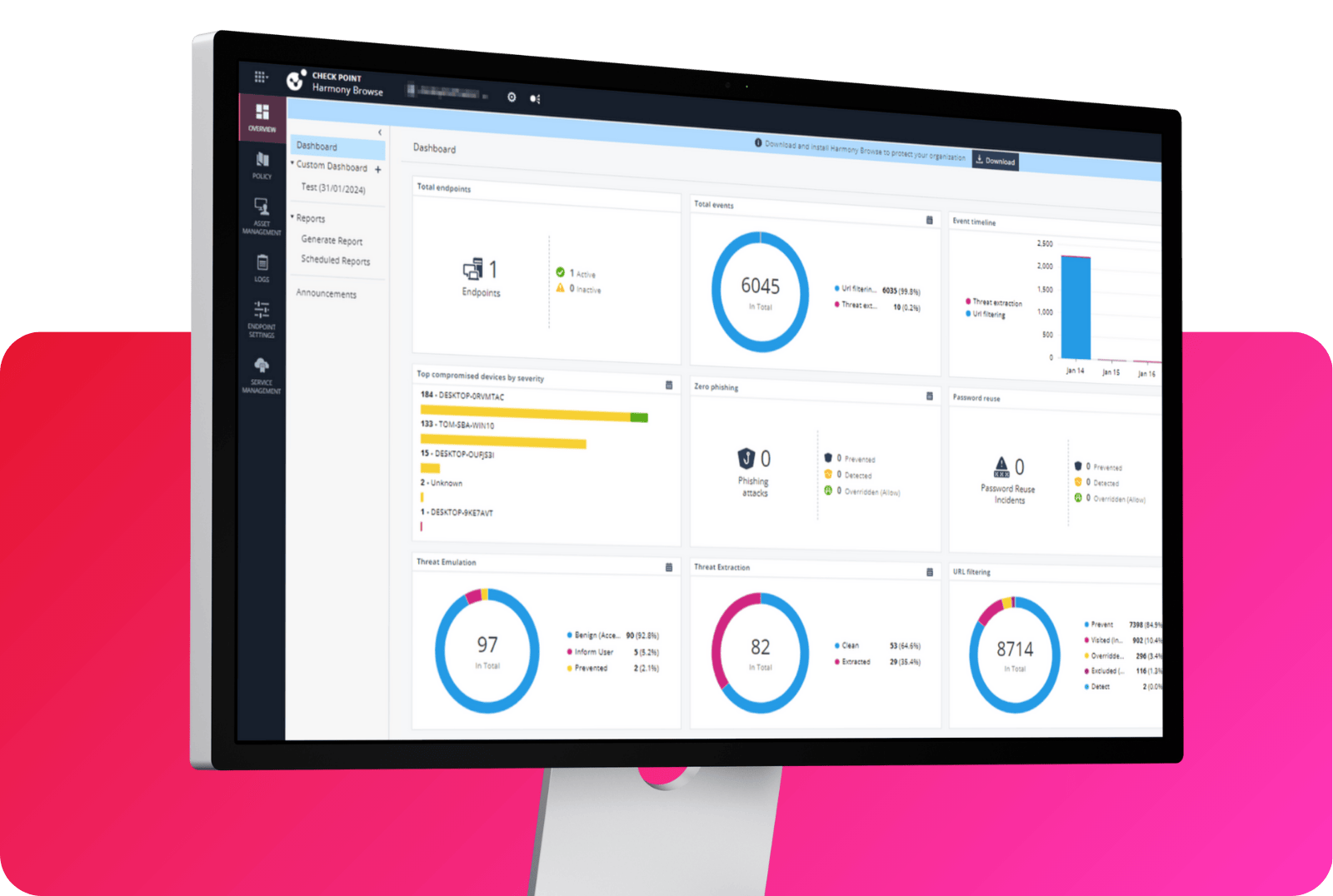
Reinventing Email Security
Check Point is revolutionizing email security. We neutralize sophisticated phishing threats before they reach end-users’ inboxes. Our advanced AI-driven algorithms analyze content in real-time, stopping the most evasive phishing attempts with unparalleled accuracy
Anti-Phishing Software
Leverage AI and ML to analyze all email components, preventing attacks ranging from ransomware and account takeover, to BEC and zero-day threats.
An API integration analyzes historical emails to identify user impersonation, stopping BEC attacks and reducing phishing by 99.2%.


Account Takeover Protection
Our event analysis algorithm identifies behavior indicative of account takeover by analyzing historical data and monitoring over 100 event indicators. Machine learning algorithms detect and prevent attacks, effectively stopping breaches.
DLP and Compliance
SmartDLP provides a structured approach to data loss prevention in emails, identifying and marking emails and instant messages containing confidential, financial, and personally identifiable information.
Flexible workflows can quarantine, alert, or encrypt sensitive emails to prevent unauthorized sharing.


Incident Response-as-a-Service (IRaaS)
Check Point’s expert analysts assess and respond to end-user reports and requests on your organization’s behalf, taking this burden off of your SOC/Help Desk
IRaaS provides expert management for end-user reports of suspicious emails and requests to release quarantined emails. Available 24/7, our team ensures fast, efficient handling of email threats, allowing your team to focus on more strategic or critical tasks